前言
上篇文章给 Burp Suite 添加验证码识别技能点,对于现代化的渗透测试神器来说,自动化切换 ip 也是必备技能,本文通过动态设置 HTTP 代理来完善此功能。
快速开发
原理分析
对于 HTTP 代理,HTTP 客户端向代理发送请求报文,代理服务器需要正确地处理请求和连接(例如正确处理 Connection: keep-alive),同时向服务器发送请求,并将收到的响应转发给客户端。
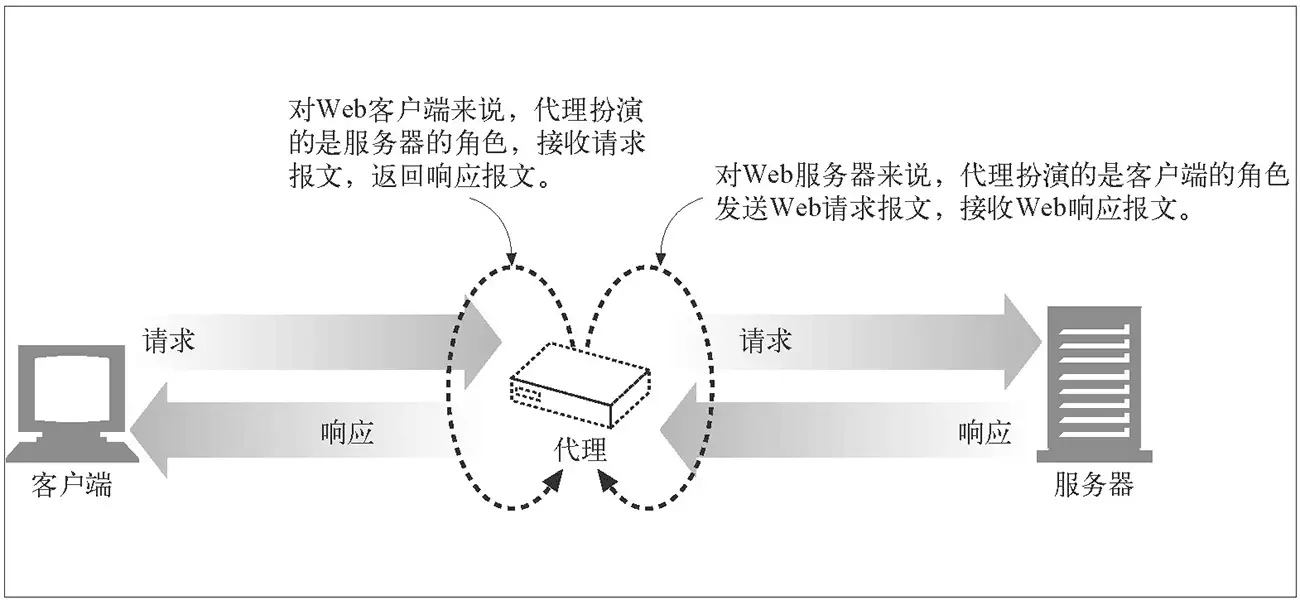
图片来源:《HTTP 权威指南》
原理较为简单,具体看数据包对比
正常访问
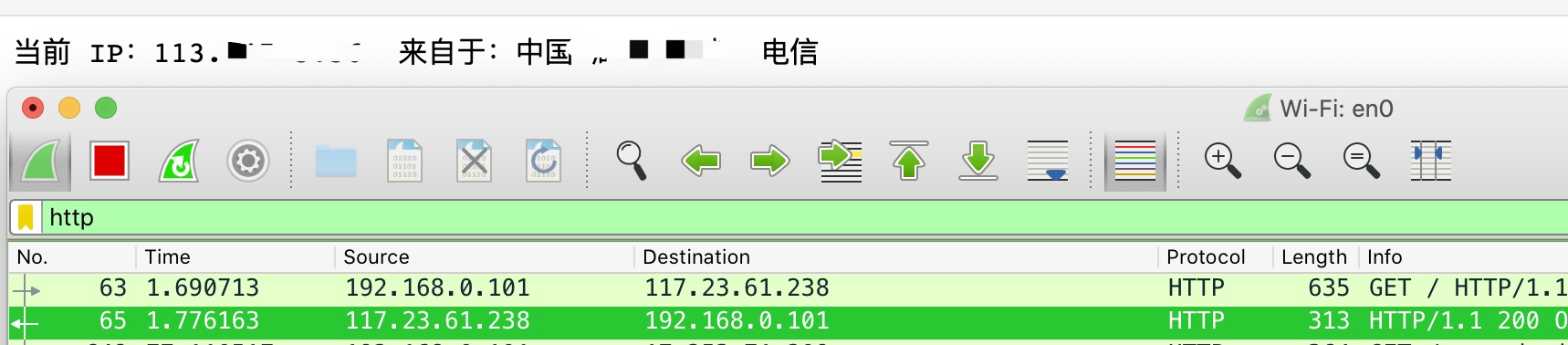
http 流
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| GET / HTTP/1.1
Host: myip.ipip.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:69.0) Gecko/20100101 Firefox/69.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
HTTP/1.1 200 OK
Date: Mon, 01 Apr 2020 16:58:35 GMT
Content-Type: text/plain; charset=utf-8
Content-Length: 67
Connection: keep-alive
...... IP...113.*.*.* .................. ...... ...... ......
|
代理访问
HTTP 代理 180.143.244.66:18637
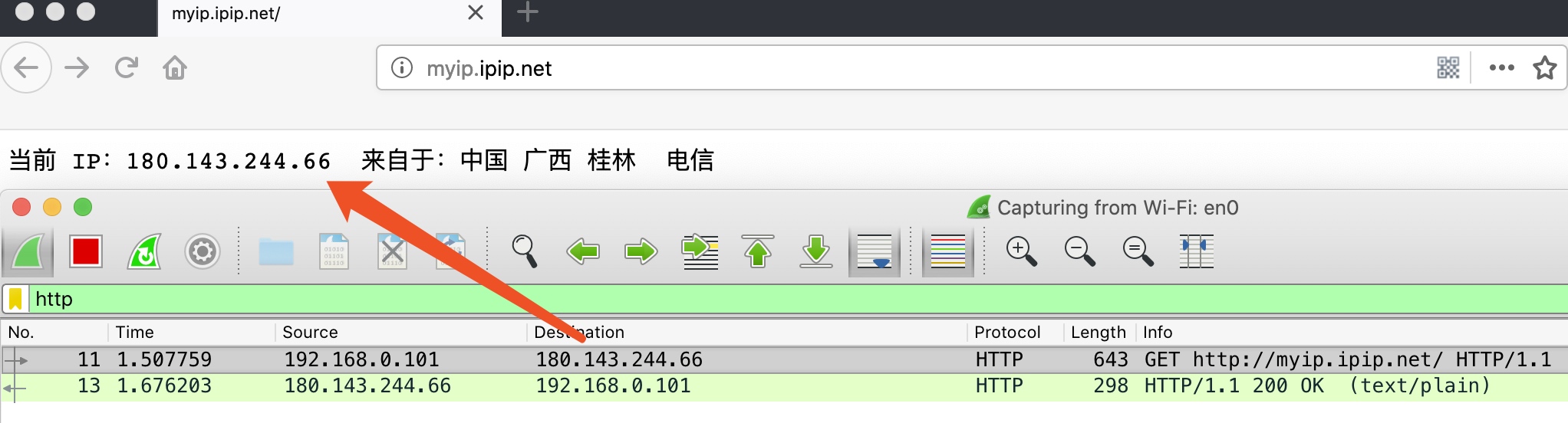
http 流
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| GET http://myip.ipip.net/ HTTP/1.1
Host: myip.ipip.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:69.0) Gecko/20100101 Firefox/69.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
HTTP/1.1 200 OK
Date: Mon, 01 Apr 2020 17:18:45 GMT
Content-Type: text/plain; charset=utf-8
Content-Length: 69
Connection: close
...... IP...180.143.244.66 .................. ...... ...... ......
|
可以看到正常访问和代理访问在数据层就是请求路径和目标不同。使用代理就是把数据带上目标信息先发送到代理服务器,要在 Burp Suite 中实现代理功能,动态修改请求目标和请求 header 即可 。
代码编写
参考官方文档,修改 HTTP 请求,需要在脚本中实例化 IHttpListener 类并重写 processHttpMessage 方法。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| HTTP_PROXY={
'ip':'14.118.163.95',
'port':19048
}
class BurpExtender(IBurpExtender, IHttpListener):
def registerExtenderCallbacks(self, callbacks):
self._callbacks = callbacks
self._helpers = callbacks.getHelpers()
callbacks.setExtensionName("IP switch")
callbacks.registerHttpListener(self)
def processHttpMessage(self, toolFlag, messageIsRequest, messageInfo):
if not messageIsRequest:
return
httpService = messageInfo.getHttpService()
messageInfo.setHttpService(
self.helpers.buildHttpService(
HTTP_PROXY['ip'],
HTTP_PROXY['port'], True
)
)
requestInfo = self.helpers.analyzeRequest(messageInfo)
new_headers = requestInfo.headers
req_head = new_headers[0]
new_headers[0] = re.sub('\/'," http://myip.ipip.net/",req_head)
body = messageInfo.request[requestInfo.getBodyOffset():len(messageInfo.request)]
messageInfo.request = self.helpers.buildHttpMessage(
new_headers,
body)
|
对接平台
接入代理平台或者 aws
实战演示
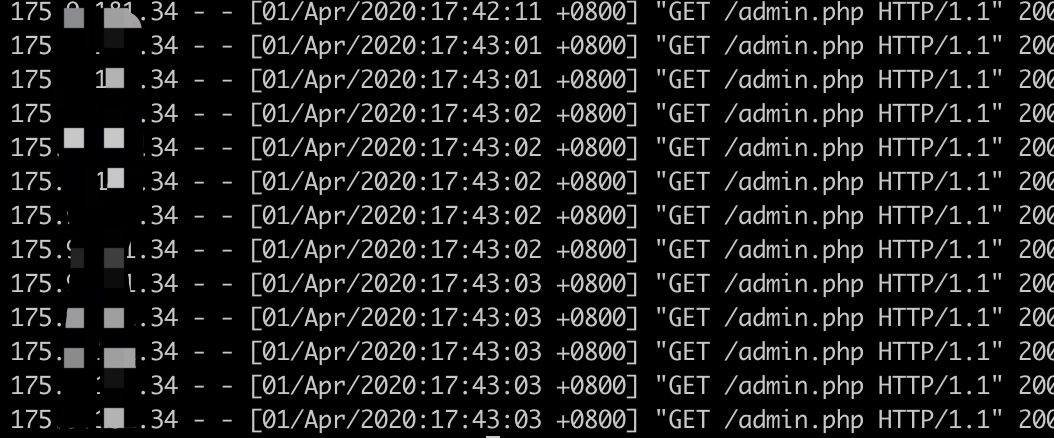
继续使用上篇后台做演示
正常访问
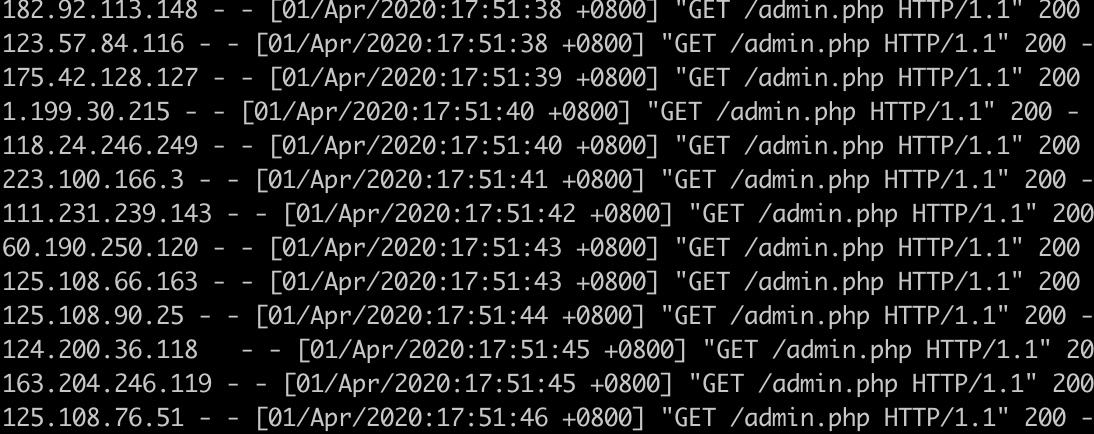
开启拓展
参考
1、HTTP 代理原理及实现(一)
https://imququ.com/post/web-proxy.html
2、 Burp Suite 文档
https://portswigger.net/burp/extender/api/burp/IHttpListener.html
3、使用AWS API 网关动态绕过防火墙
https://rhinosecuritylabs.com/aws/bypassing-ip-based-blocking-aws/





